must read
Blackbox transforming online anonymity market: cases comparisons with old-school solutions
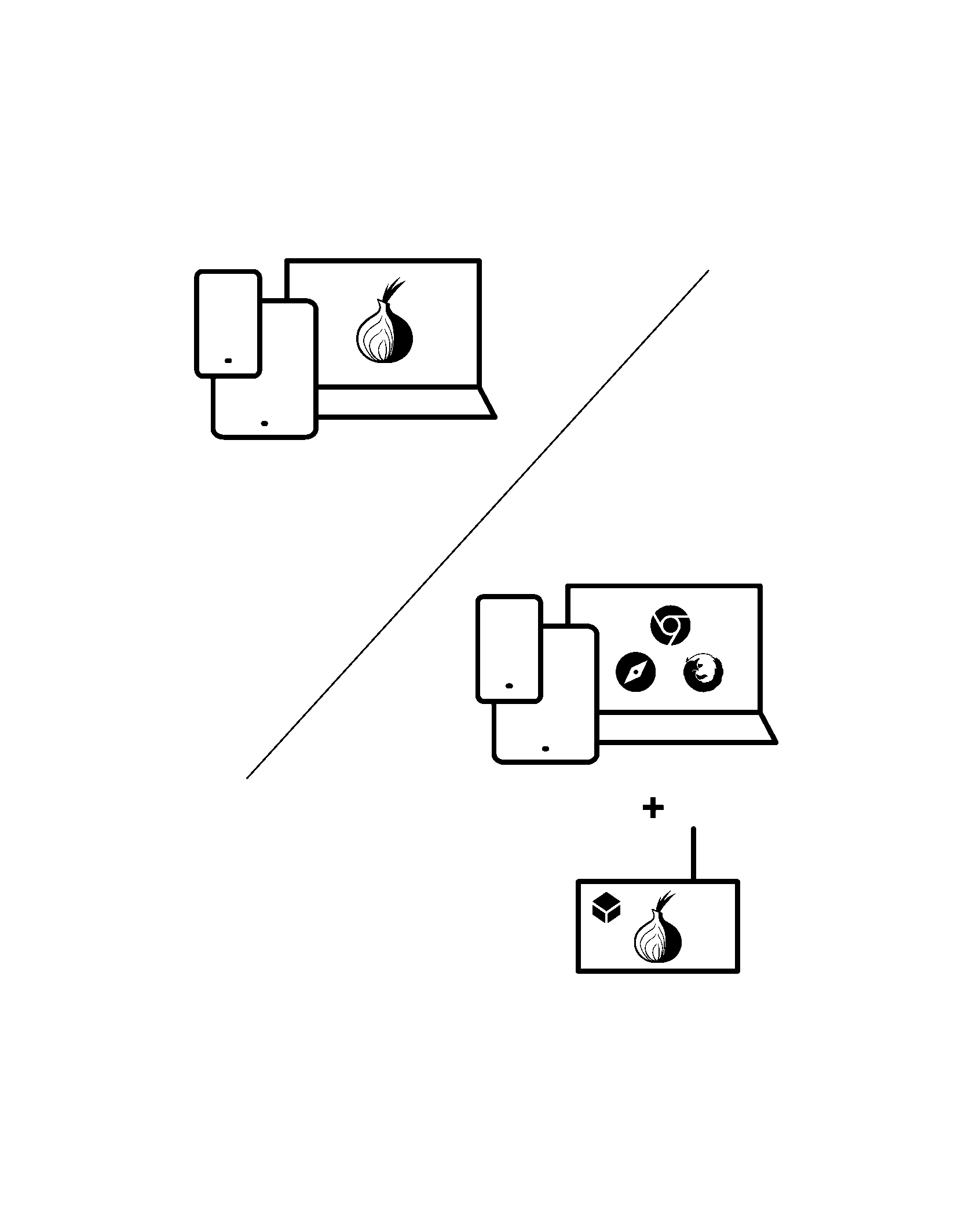
TOR on your PC VS TOR on your Blackbox
Crypto wallets, VPN and other services that require anonymity
Make cryptocurrency transactions or browse darknet anonymously and safely
When you are browsing darknet or performing cryptocurrency operations on your PC, your actions are compromised by the operating system (Windows, macOS, etc.), and some of the installed programs, such as an antivirus.
Blackbox is designed and configured so that nothing could compromise you.
When you are browsing darknet or performing cryptocurrency operations on your PC, your actions are compromised by the operating system (Windows, macOS, etc.), and some of the installed programs, such as an antivirus.
Blackbox is designed and configured so that nothing could compromise you.
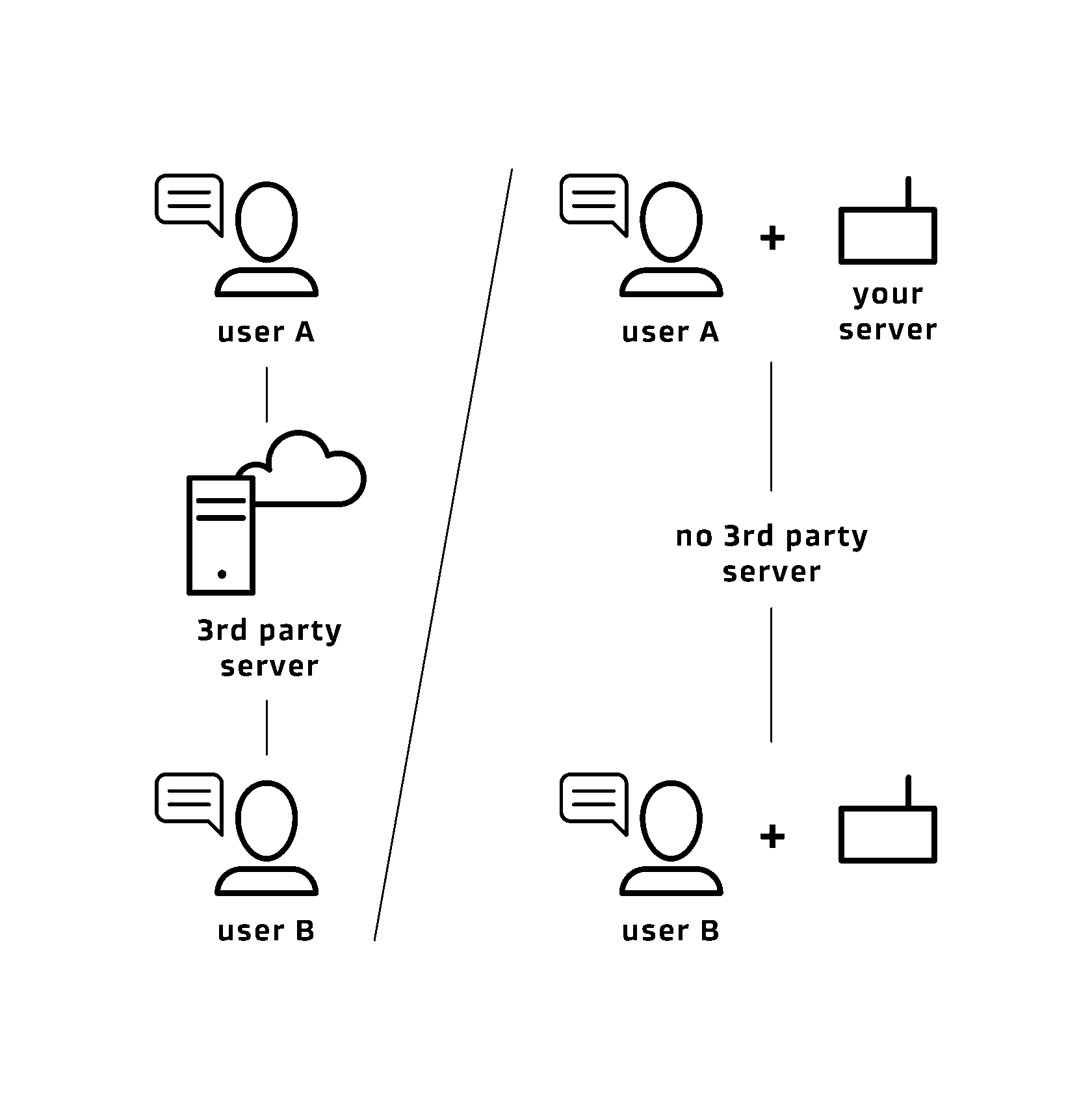
Other secure messengers vs your Blackbox messenger
Do not confide your conversations to those services that you cannot verify.
When you use messengers such as Telegram, Signal, or WhatsApp for texting or making calls, your data is transmitted over these apps servers with closed architecture. No one can make sure that the servers do not save and analyze your data. Therefore, when using these applications, you take it on trust that they really guarantee privacy.
When you are communicating via Blackbox xmpp messenger, Blackbox serves as a server. In this case, you have physical access to the server and can make sure in your anonymity. Moreover, you register accounts for the people you talk to without reference to their phone number or personal data.
When you are communicating via Blackbox xmpp messenger, Blackbox serves as a server. In this case, you have physical access to the server and can make sure in your anonymity. Moreover, you register accounts for the people you talk to without reference to their phone number or personal data.
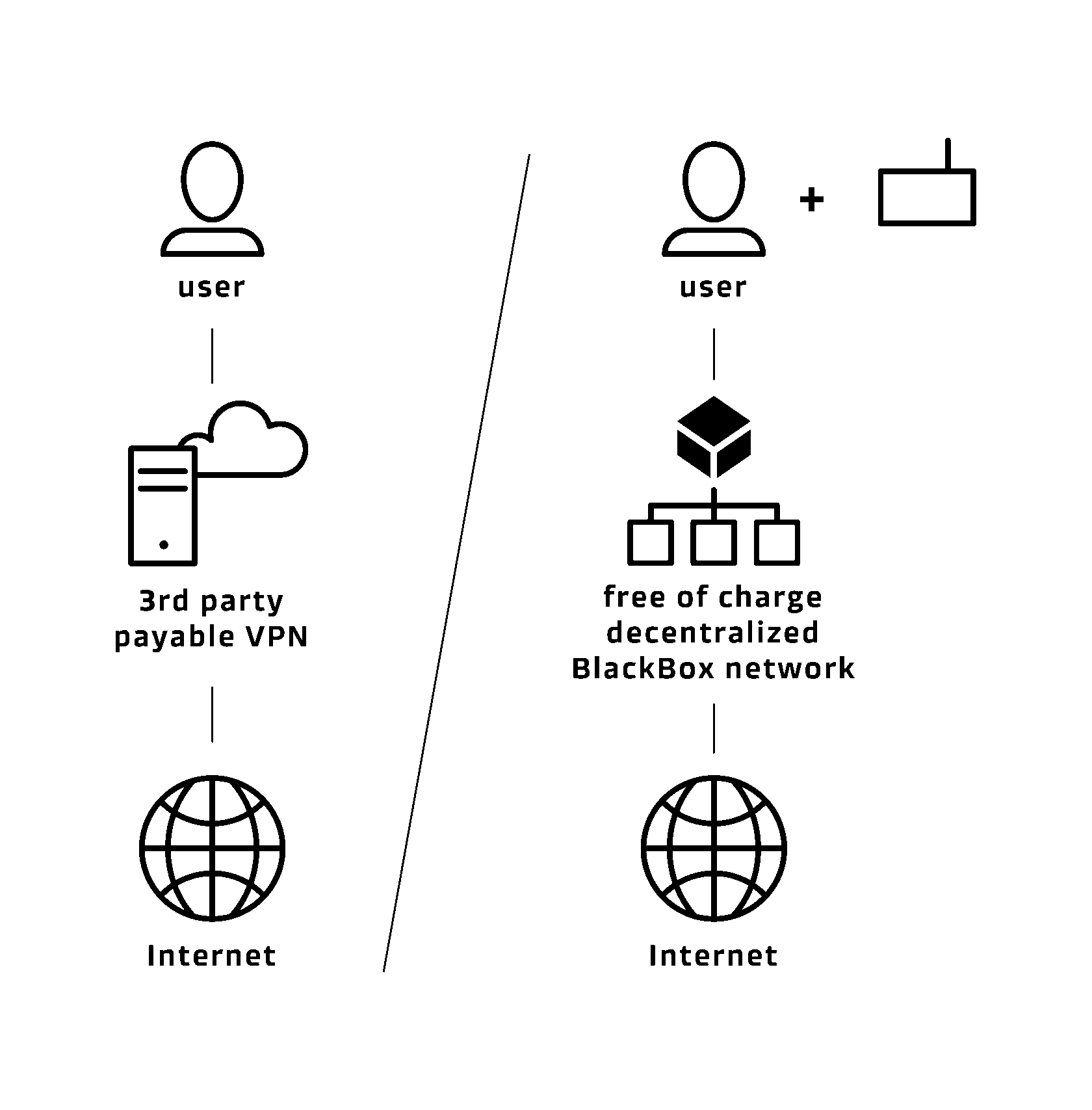
Centralized classic VPN vs decentralized Blackbox VPN
Which service is cheaper?
Classic VPN - from 70 euros per year
Blackbox VPN - free of charge
When it is more likely that your data will be collected?
Classic VPN - your data is transmitted over a centralized server of a commercial organization.
Blackbox VPN - your data is transmitted over a random BB user whose Blackbox has the same configurations as yours
Which server you trust more?
Server to which you have no access and thus you can not verify your confidentiality.
Server which has the same configurations as your Blackbox.
Data transmitted over the device of a random Blackbox user is completely secure. The transmission device has no reference to a user, and the transmitted data is encrypted.
Classic VPN - from 70 euros per year
Blackbox VPN - free of charge
When it is more likely that your data will be collected?
Classic VPN - your data is transmitted over a centralized server of a commercial organization.
Blackbox VPN - your data is transmitted over a random BB user whose Blackbox has the same configurations as yours
Which server you trust more?
Server to which you have no access and thus you can not verify your confidentiality.
Server which has the same configurations as your Blackbox.
Data transmitted over the device of a random Blackbox user is completely secure. The transmission device has no reference to a user, and the transmitted data is encrypted.
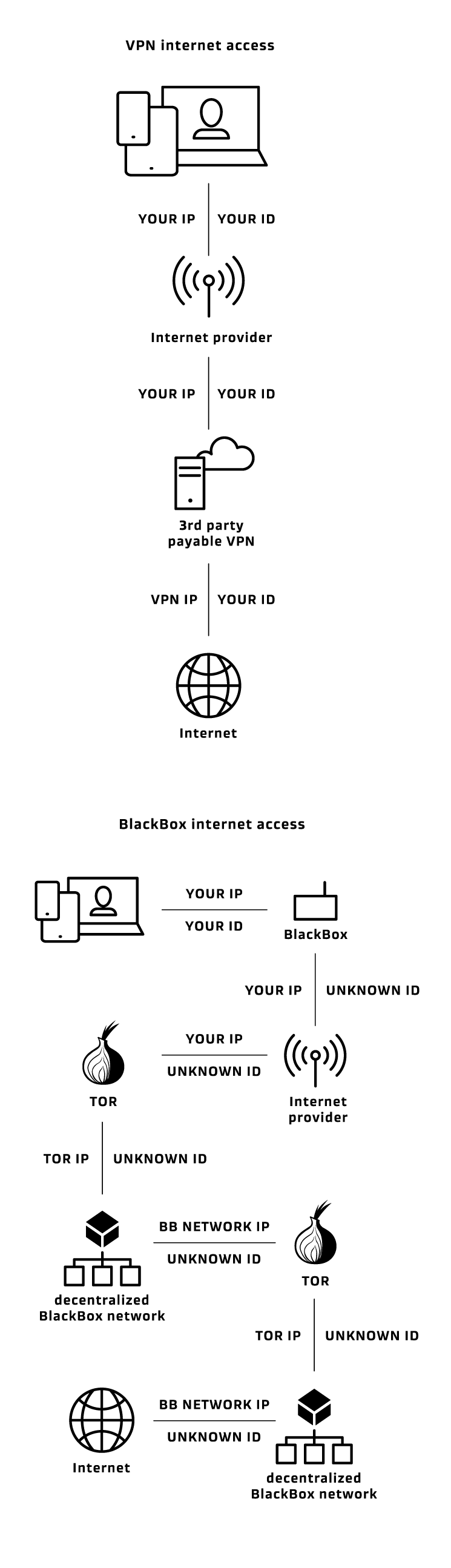
Hiding your identity using VPN vs hiding your identity using Blackbox
Why Blackbox is the missing element in the existing anonymity solutions?
Going online using VPN
1. Data from your device is transmitted to the Internet service provider
2. Internet service provider:
- identifies you by the ID of your device
- defines your location and the web resource (VPN server) you are attempting to connect.
3. The Internet service provider sends the request to a VPN server
VPN server:
1. hides your IP address from the Internet resources you have connected by substituting it with the VPN IP address. However, it's not enough to ensure complete security.
2. VPN services do not provide opportunities to check that your personal data is not stored or used. VPN service providers declare that they do not collected any data transferred over their servers. But we cannot confirm or deny this fact, since there is no physical or remote access to their servers. VPN service providers do not grant access to their servers configurations and the software they use to the third parties.
Using VPN means that you cannot verify the security of VPN services and give access to your confidential information, entrust your security to unknown people by simply taking the word for it.
3. The Internet resource may request to identify the person who connected to it. In this case, there are at least two ways to do that (in both of them the Internet resource obtains the device ID, the VPN IP address, connection date and time):
1. If VPN service collects and stores user personal data, it can provide the IP address of the user that connected to VPN network at a specific time and was edirected to a particular web resource - you are compromised.
2. If VPN service do not collect and store user personal data:
a) VPN hides only IP address, the device ID remains unchanged.
b) by law, Internet service providers store all user data in the database, which make it possible to identify the IP address and device ID of the user who connected to the VPN server at a particular time - you are compromised.
How Blackbox provides anonymity and confidentiality?
1. BB prevents the third party services from identifying the user. Device ID has no reference to a user's personal data, which make it impossible to identify who is going online.
Despite Blackbox ID is changed during each reboot, for security reasons you cannot open your accounts in other services and apps because it can connect your Blackbox ID with your personal data via your profiles credentials. You can set new accounts in any apps or services you need when going online with Blackbox, but you should keep in mind that using them on other devices later make it possible to identify you.
2. BB makes it impossible to define your location. When going online with BB, you connect to a secure Blackbox TOR network. Before connecting you to any Internet resource, BB makes 5 redirects within this network. VPN or Proxy services hide your IP address making only one redirect, and it allows to define the source of traffic easily. BlackBox generates 5 in the 5 power of possible location options all over the world, and thus securely hides your real location.
3. Operating system cannot track your activities, collect any information or interfere with anonymization software.
4. The data is encrypted before being transmitted, therefore the third parties cannot track your activities. We use the forefront verified encryption algorithms, such as OTR, OMEMO, SSH 256/512.
5. Blackbox automatically removes all data related to each session during reboot. So even if someone gets hold of your password, you still won't be compromised
6. The memory card is protected from reading by other devices. If someone gets physical access to your phone or PC, he or she can obtain all your data (even if it was deleted) no matter if your device is protected with a password or not. For this purpose, it's enough to extract the memory card or hard drive and connect it to equipment that restores data. Blackbox memory card is covered with mastic-like epoxy adhesives which makes the extraction impossible.
1. Data from your device is transmitted to the Internet service provider
2. Internet service provider:
- identifies you by the ID of your device
- defines your location and the web resource (VPN server) you are attempting to connect.
3. The Internet service provider sends the request to a VPN server
VPN server:
1. hides your IP address from the Internet resources you have connected by substituting it with the VPN IP address. However, it's not enough to ensure complete security.
2. VPN services do not provide opportunities to check that your personal data is not stored or used. VPN service providers declare that they do not collected any data transferred over their servers. But we cannot confirm or deny this fact, since there is no physical or remote access to their servers. VPN service providers do not grant access to their servers configurations and the software they use to the third parties.
Using VPN means that you cannot verify the security of VPN services and give access to your confidential information, entrust your security to unknown people by simply taking the word for it.
3. The Internet resource may request to identify the person who connected to it. In this case, there are at least two ways to do that (in both of them the Internet resource obtains the device ID, the VPN IP address, connection date and time):
1. If VPN service collects and stores user personal data, it can provide the IP address of the user that connected to VPN network at a specific time and was edirected to a particular web resource - you are compromised.
2. If VPN service do not collect and store user personal data:
a) VPN hides only IP address, the device ID remains unchanged.
b) by law, Internet service providers store all user data in the database, which make it possible to identify the IP address and device ID of the user who connected to the VPN server at a particular time - you are compromised.
How Blackbox provides anonymity and confidentiality?
1. BB prevents the third party services from identifying the user. Device ID has no reference to a user's personal data, which make it impossible to identify who is going online.
Despite Blackbox ID is changed during each reboot, for security reasons you cannot open your accounts in other services and apps because it can connect your Blackbox ID with your personal data via your profiles credentials. You can set new accounts in any apps or services you need when going online with Blackbox, but you should keep in mind that using them on other devices later make it possible to identify you.
2. BB makes it impossible to define your location. When going online with BB, you connect to a secure Blackbox TOR network. Before connecting you to any Internet resource, BB makes 5 redirects within this network. VPN or Proxy services hide your IP address making only one redirect, and it allows to define the source of traffic easily. BlackBox generates 5 in the 5 power of possible location options all over the world, and thus securely hides your real location.
3. Operating system cannot track your activities, collect any information or interfere with anonymization software.
4. The data is encrypted before being transmitted, therefore the third parties cannot track your activities. We use the forefront verified encryption algorithms, such as OTR, OMEMO, SSH 256/512.
5. Blackbox automatically removes all data related to each session during reboot. So even if someone gets hold of your password, you still won't be compromised
6. The memory card is protected from reading by other devices. If someone gets physical access to your phone or PC, he or she can obtain all your data (even if it was deleted) no matter if your device is protected with a password or not. For this purpose, it's enough to extract the memory card or hard drive and connect it to equipment that restores data. Blackbox memory card is covered with mastic-like epoxy adhesives which makes the extraction impossible.